Detecting Rogue LLMNR
How Hackers steal credentials inside your networking without moving a finger and how to prevent it?
Link-Local Multicast Name Resolution (LLMNR) is a protocol that is used to enable name resolution of hostnames to IP addresses on a local network in the absence of a Domain Name System (DNS) server. This protocol serves as a fallback mechanism when DNS resolution fails. LLMNR is often used by administrators to troubleshoot DNS name resolution issues and is enabled by default on Windows operating systems.
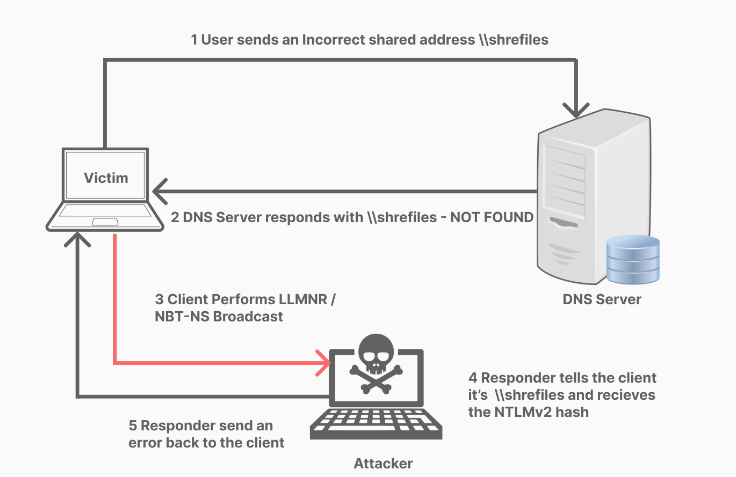
However, this protocol can also be exploited by attackers to conduct attacks like Man-in-the-Middle (MitM) and network reconnaissance. Rogue LLMNR servers respond to LLMNR name resolution requests from hosts on the network and can be used by attackers to intercept and steal sensitive information, as well as perform other malicious activities.
This is where Responder comes in. It is an open-source, cross-platform command-line tool used for network analysis, penetration testing, and security assessment. Responder is a collection of various tools and scripts that can be used to extract sensitive information such as usernames and passwords, perform MitM attacks, and perform other network reconnaissance tasks.
Responder can detect and respond to various network protocols such as LLMNR, NBT-NS, and mDNS, and can be used to exploit vulnerabilities in these protocols. It works by creating a fake network service that mimics legitimate services, such as LLMNR, and waits for clients to connect. Once a client connects to the fake service, Responder captures and logs any authentication credentials sent over the network, allowing an attacker to obtain sensitive information. In the figure below we demonstrate how responder can capture a NTLMv2 Hash which we can then try to crack using hashcat.
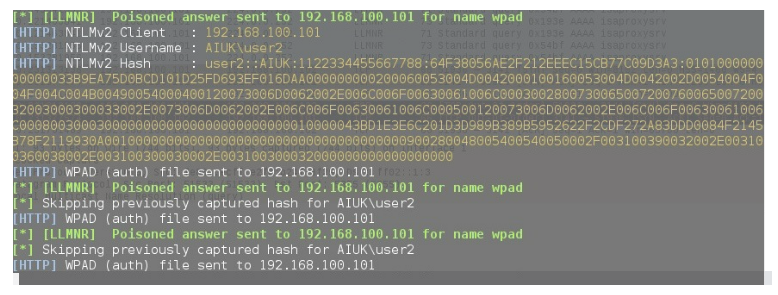
Creating a honeypot to detect rogue LLMNR
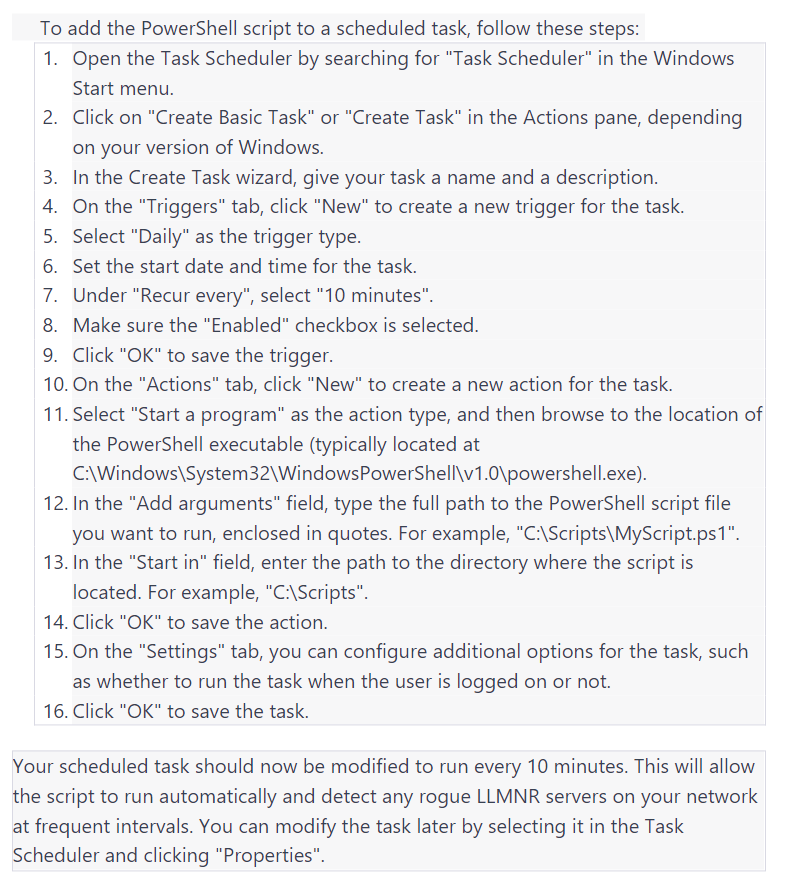
The PowerShell script mentioned below can be used as a honeypot to detect rogue LLMNR servers on a local network. A honeypot is a decoy system that is designed to detect, deflect, or counteract attempts at unauthorized use of information systems. In the context of LLMNR, a honeypot can be used to simulate a host on the network that sends out LLMNR queries and detects rogue LLMNR servers. The script sends out an LLMNR query for a nonexistent hostname and checks if a response is received. If a response is received, it means that a rogue LLMNR server is present on the network, and the script logs a warning event in the Windows Application event log. This can be useful in detecting and preventing attacks on the network, as it allows administrators to identify and remove rogue LLMNR servers before they can be used by attackers to exploit vulnerabilities in the LLMNR protocol. By using this honeypot method, network administrators can proactively secure their networks against LLMNR-based attacks and minimize the risk of data theft and other security breaches.
$llmnr = (Resolve-DnsName -LlmnrOnly NOTEXISTING 2> $Null)
if ($llmnr) {
$ip = $llmnr.IpAddress -Join ","
$msg = "Hostname: ${env:computername}`nRogue LLMNR Server: $ip"
Write-eventLog -LogName Application -Source ResponderPot -EventId 9001 -Message $msg -EntryType Warning
}
An explanation of the PowerShell script above
- The first lines sets a variable named $llmnr by running the Resolve-DnsName cmdlet with the -LlmnrOnly parameter and an invalid hostname (NOTEXISTING). The purpose of this is to force Resolve-DnsName to only use LLMNR for name resolution, rather than other protocols like DNS or WINS. If a rogue LLMNR server is present on the network, it may respond to this query and provide an IP address for the nonexistent hostname. The 2> $Null portion of the command redirects any error output to null, so that errors are not displayed on the console.
- The if statement checks whether the $llmnr variable is not null. If it is not null, this means that a response was received from an LLMNR server, indicating the presence of a rogue LLMNR server on the network.
- The script then extracts the IP address from the $llmnr variable and joins them together into a comma-separated string using the -Join operator.
- The script constructs a message that includes the name of the local computer and the IP address of the rogue LLMNR server.
Finally, the script logs a warning event in the Application event log using the Write-EventLog cmdlet. The event is sourced from ResponderPot with an event ID of 9001 and a message of the constructed message.
Vital to understand the potential security risks
In conclusion, it is vital to understand the potential security risks posed by rogue LLMNR servers in today’s digital age. These servers can compromise your network’s security and allow attackers to intercept traffic and steal sensitive information. We showed how the responder tool can be used to collect NTLM hashes. Additionally, we also showed how to detect rogue LLMNR server using the custom PowerShell scheduled task discussed in this article. By implementing these measures, you can help keep your network and data safe from potential security breaches.
We realize the information above is very technical. If you need any assistance with implementing this extra security measure, or for any other questions, please do not hesitate to contact us. Our Cyber Security consultants are always happy to help out.
Reduce Risk, Create Value!