The Current Situation of Malware
The Current Situation
Malware is widespread today and poses a significant threat to individuals and businesses. The most widespread type of cyberattacks, they include viruses, worms, Trojans, spyware, and ransomware. A system is usually infected with malware via a link on an unreliable website, an email or an unwanted software download. Social engineering is one of the most commonly used techniques for targeted malware attacks. It settles on the target system, collects private information, manipulates and denies access to network components, and has the potential to delete data or shut down the system completely. Each type of malware has its own characteristics and purposes, but they all have the potential to cause serious damage to your digital devices and data.
Viruses
Computer viruses are designed to disrupt systems and cause significant malfunctions and data loss and leakage. It is important to understand that computer viruses are designed to spread between systems and programs. Computer viruses often attach themselves to a host executable when a file is opened, causing its viral code to run. The code is then propagated through the accompanying software or document via networks, drives, file-sharing applications, or malformed email attachments.
Worms
A computer worm is a subset of Trojan horse malware that, once infiltrating a system, can spread or self-replicate from one computer to another without human activation. A worm often spreads over a network using your LAN (Local Area Network) or Internet connection.
Trojans
Malware that poses as trustworthy programs or software is known as a Trojan Horse (Trojan). Attackers have access to all actions that a legitimate user could perform once they are within the network, including exporting files, editing data, deleting files, and otherwise changing the contents of the device. Trojans may come pre-installed with game, tool, app, or even software patch downloads. To get the user to take the intended action, many Trojan assaults also include spoofing, phishing, and social engineering techniques.
Ransomware
Malware known as ransomware uses encryption to demand a ransom for access to a victim’s data. Critical data for a user or organization is encrypted to prevent access to files, databases, or applications. Then access is sought in exchange for a ransom. Ransomware can easily shut down an entire company since it is frequently made to propagate over a network and target database and file servers. It is an expanding menace that brings in billions of dollars in payments to hackers while causing serious harm and high costs for businesses and governmental institutions.
Spyware
Spyware is malicious software that infiltrates a user’s computer, collects information about the user and the device, and then distributes it to other parties without the user’s knowledge or agreement. A piece of malware created to access and harm a device without the user’s permission is typically understood as spyware.
It gathers private and sensitive data that it sells to advertising, data gathering companies, or unscrupulous individuals in order to make money. Attackers use it to trace, take, and sell user information such internet activity patterns, credit card numbers, and bank account information, as well as to steal user credentials to impersonate users.
Adware
Any product application known as “adware” displays unwanted advertising banners while a piece of software is running. The promotions are displayed as pop-up windows or bars on the user interface of the software. Adware is often created for computers, however it can also be found on mobile devices. Adware makes money for its creator by automatically displaying web adverts in the software’s user interface or on a screen that appears in front of the user while the user is installing it. And that’s when you start seeing questionable get-rich-quick schemes, promises for weight loss miracles, and fake virus alerts that beg you to click on them. Additionally, you may notice that new tabs appear, your home page changes, results from a search engine you’ve never heard of, or even a reroute to an NSFW website.
Fileless malware
Malicious code known as “fileless malware” doesn’t need to use any additional executable files on the endpoint’s file system beyond those that are already present. Usually, it is introduced into an active process and just RAM is used for execution. Due to the small footprint and lack of files to scan, this is much more difficult for standard antivirus software and other endpoint security products to identify or block.
Rootkits
Rootkits are malicious software programs that give threat actors remote access to and control over a computer or other device. The majority of rootkits unlock a backdoor on victims’ systems, allowing malicious software, such as keylogger programs, viruses, or ransomware, to be installed for network security assaults, despite the fact that some rootkits have legal functions, such as providing additional end-user assistance. In order to prevent malicious software from being discovered, rootkits commonly disable antivirus software, endpoint security systems, and anti-malware.
User-mode rootkits
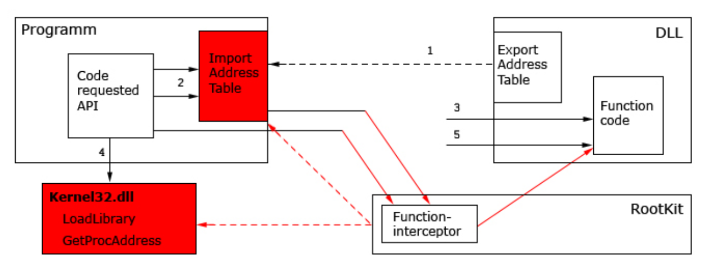
These rootkits run their programs in privileged user mode (also known as “Ring 3” [9]). These rootkits make advantage of plugins and application extensions (e.g. Windows Explorer or Internet Explorer extensions). They can employ a debugger, exploit security flaws, and use function hooking of popular APIs in every process’ data sets. They can even intercept interrupts.
Over the years, we have seen several high-profile malware attacks, including the WannaCry ransomware attack that affected over 200,000 computers worldwide and the Equifax data breach, which compromised the personal information of over 140 million people. These attacks highlight the need for better protection against malware and the importance of staying vigilant in today’s digital landscape.
ILOVEYOU Virus (2000)
In May 2000, millions of computers were infected with the ILOVEYOU virus, sometimes referred to as the Love Bug. It was one of the most significant viruses in computer history, affecting approximately 50 million computers within 10 days, accounting for 10% of all computers worldwide.
The Creator of the Virus
Onel de Guzman, a Filipino computer science student, developed the ILOVEYOU malicious software with the use case of stealing user credentials from websites. He developed malicious software that sent the credentials stolen from victims’ computers to an email address he controlled. The virus spread rapidly, millions of computers around the world were infected with the malware.
The Destructive Impact of the Virus
The ILOVEYOU Virus is considered by many as one of the most damaging and destructive computer viruses ever developed. It affected major institutions and businesses such as the British parliament, Pentagon, and several major banks. With and estimated 15$ billion in global damages it is hard to say otherwise.
How the Virus Spread
By exploiting a Windows vulnerability, which allowed to rewrite of data on the infected computers and spread to other computers via email. The user would get a simple email with the subject: “ILOVEYOU” and the text, “Please check the attached LOVELETTER from me.” Due the Microsoft vulnerability, the user would get infected just by opening the email.
VBScript and Hidden Extensions
This malware is, in essence, a VBScript program. Visual Basic Script, sometimes known as VBScript, was created by Microsoft as a simplified version of Microsoft Visual Basic, with which it shares the majority of its source code. Because the virus’s file name was “LOVE-LETTER-FOR-YOU.TXT.vbs,” it’s also known as “Love letter for you.” Because the creator of the ILOVEYOU virus exploited a flaw in the Windows 95 email system and disguised the extension when the file name appeared in attachments, the name appeared hidden with the true “.vbs” extension. The title includes a phony “.txt” extension to fool the receiver into thinking he was about to open a text file.
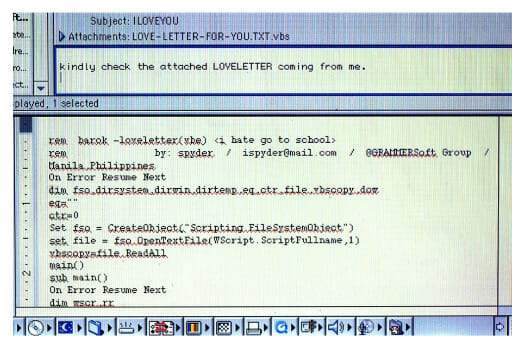
The Virus in Action
When a user’s computer was infected, the Love Letter virus started Microsoft Outlook and sent copies of itself to all of the contacts in their address book. It swiftly swept throughout all Internet-connected PCs in this way, even business networks. As was already explained, the virus propagated to other computers and corrupted files, rendering them useless. In an effort to avoid the threat, many significant companies and government agencies, including the CIA and the Pentagon, shut down their email networks.
The ILOVEYOU virus served as a wake-up call, underlining the risks of email attachments and the demand for better security procedures to fend off malware. The first serious “pandemic” of computer viruses that altered cybersecurity as we know it was this one.
Stuxnet – the first known cyber ‘weapon’ (2010)
Stuxnet, a computer worm discovered in 2010, is widely regarded as one of the most complex and destructive pieces of malware ever devised.
What is Stuxnet?
Stuxnet is a computer worm that specifically targets industrial control systems used in Iran’s nuclear program. It was part of a high-level sabotage campaign waged by nation-states against their adversaries. Certain Siemens programmable logic controllers (PLCs) were programmed to fail as a result of Stuxnet, potentially causing damage to Iran’s nuclear centrifuges.
How dows Stuxnet work?
Using a stolen digital certificate, the worm took advantage of a flaw in the Windows operating system and disguised itself as a valid software update. It looked for and infected particular Siemens PLCs when it was installed. The worm contaminated centrifuges, causing them to malfunction and potentially cause injury. Stuxnet was developed to precisely target the Siemens Step7 software used in the nuclear program and was written in a variety of computer languages, including C and C++. It also used a rootkit to hide its existence on infected systems and spread via removable media like USB drives.
The main “dropper”, installer from the USB drive, the ~WTR4132.TMP file.
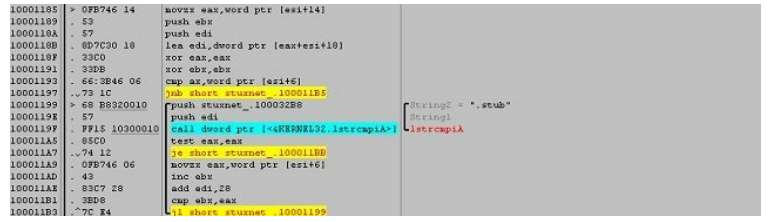
This file would load into explorer.exe, as a dynamic library file and would begin its execution by searching for a section in it which contained all the Stuxnet’s functions, mechanisms, files and rootkits. This section was named “.stub” containing the DLL file.
Who created Stuxnet?
Stuxnet was developed collaboratively by Israel and the United States to hinder Iran’s nuclear program. The worm was designed primarily to damage Iran’s nuclear centrifuges.
What vulnerability did Stuxnet exploit?
Stuxnet leveraged a number of previously undiscovered Windows zero-day vulnerabilities, allowing it to avoid detection and propagate across computer networks.
How was Stuxnet discoverd?
In June 2010, VirusBlokAda, a Belarusian antivirus company, discovered Stuxnet. Further investigation revealed the true capabilities of the virus and its intended use, after it was initially thought to be a very simple infection.
As a result of the discovery of Stuxnet, which sparked global concern about potential cyberattacks on critical infrastructure, there was an increased effort to improve the security of industrial control systems. In addition, the discovery highlighted the growing importance of cybersecurity in modern warfare and the possibility that cyberattacks could have negative effects in the real world. Stuxnet is a sobering reminder of the capability and potential danger of software used as a weapon.
Wanacry ransomware (2017)
On May 12, 2017, one of the most devastating cyberattacks in the history of the Internet began. The WannaCry ransomware attack. More than 200,000 computers in 150 countries were infected and locked out of their files. The attack spread quickly and caused massive disruption to businesses, hospitals, and government agencies around the world.
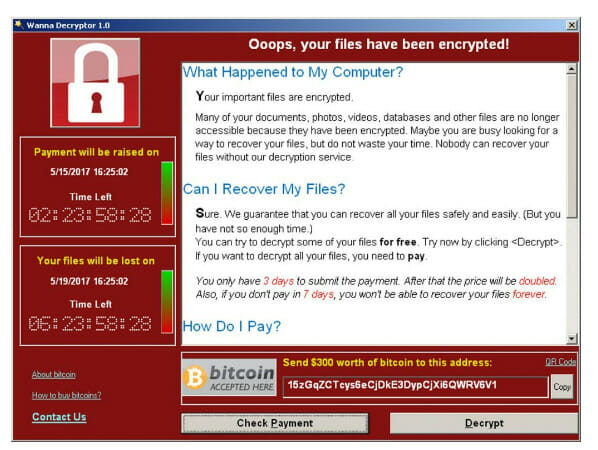
The WannaCry ransomware encrypted the victim’s files and demanded payment in exchange for the decryption key. The WannaCry ransomware explicitly demanded Bitcoin as payment. This makes it hard to trace, if not untraceable.
Who was behind the attack?
The exact perpetrators behind the WannaCry attack are still unknown, but it is believed that the attack was carried out by a North Korean hacking group called Lazarus Group.
How did WannaCry spread?
WannaCry took advantage of the EternalBlue vulnerability revealed by the US National Security Agency (NSA) in Microsoft Windows operating systems. A group known as Shadow Brokers published the weakness, which allowed WannaCry attackers to use it to quickly distribute the ransomware. The assault, which uses a worm-like approach to spread over networks, is incredibly contagious.
What were the consequences of the attack?
The WannaCry attack caused widespread chaos and disruption, affecting critical infrastructure such as hospitals and transportation systems. The U.K.’s National Health Service (NHS) was hit particularly hard, with 48 of its trusts affected, leading to the cancellation of 19,000 appointments and surgeries. The attack also caused financial losses estimated at several billion dollars.
How was WannaCry stopped?
Security researcher Marcus Hutchins uncovered a “kill switch” in the WannaCry ransomware code that can be used to prevent the malware from spreading. The kill switch is essentially a domain name that, once registered, stops the infection from propagating. Hutchins registered the domain name, essentially halting WannaCry’s spread. It was, however, too late to undo the harm that had already been done.
In conclusion, the WannaCry ransomware attack acted as an essential wake-up call for the rest of the globe to prioritize cybersecurity. It emphasized the necessity of frequently upgrading software, using secure passwords, and storing up vital data. It also emphasized the significance of international cooperation in countering cyber dangers that might harm anyone in the world.
Conclusion
We learned about some of the most common types of malware and how they function, as well as examples of malware that has had the largest impact in the last 20 years. Countries are now developing malware as “undercover” tools to be used against other countries or terrorist organizations. When these governments are hacked, some of these tools end up in the wild, causing harm to ordinary computer users. That begs the question of how moral it is for governments to build cyber weapons that exploit specific weaknesses in our networks, systems and are utilized for assaults we never learn about, putting everyone’s safety at risk. Instead of disclosing them to software vendors, hardware manufacturers should remedy these exploits that lead to malware. In the following blog post, we will discuss how malware normally works and is deployed, as well as how I constructed a proof of concept MacOS “malware” to gain a better understanding of the subject and share what I learned. In the fourth blog we give tips on how to protect your organisation against malware. Curious about the history of malware? Then read our previous blog here.
Prevent your organisation from becoming a victim of malware too? Then start mitigating the risks immediately. The Cyber Security experts of Cuccibu are ready to help! For example, we can set up an awareness programme to raise awareness about the dangers of malware among employees. We can also implement crisis simulation and/or provide SIEM/SOC monitoring. SIEM/SOC monitoring makes it possible to act as quickly as possible in case of infection and stop the attack immediately.
Want to know more about what we can do? Feel free to contact us at sales@cuccibu.nl. We will be happy to tell you about the various possibilities.
Reduce Risk, Create Value!