The Technical Aspects of Malware
The operation of Malware
Malware authors use a variety of techniques to escape detection and spread their programs. They can, for example, use social engineering techniques to trick consumers into downloading and launching malicious apps. They can also use polymorphic code, which changes the structure of the code, to avoid detection by antivirus software.
Malware can also enter devices by exploiting flaws in software or operating systems. For example, the WannaCry ransomware attack propagated by exploiting a weakness in older versions of Microsoft Windows.
Consider the operation of ransomware. What processes does it run and how? In this section, we will try to replicate how the majority of ransomware software programs work in theory. At least in terms of its logic. Understanding how malware works, contributes to awareness of Cyber Security.
General delivery of ransomware
Here is a simplified step-by-step explanation of how ransomware typically works:
- Delivery. As the first stage of a ransomware attack, the malware needs to be delivered to the victim’s computer. The most used techniques are social engineering which will make the victim open or download a malicious email attachment, phishing URLs, contaminated software, and exploit kits that exploit software defects.
- Activation. Once the ransomware has been delivered to the victim’s computer, it must be activated for the encryption process to begin. This can happen via opening a malicious attachment, clicking on a link, or just visiting an infected website. Downloading and running pirated software is one of the most common reasons victims get infected.
- Encryption. Once activated, the ransomware will start encrypting files on the victim’s computer using a strong encryption algorithm such as AES or RSA. The process can take some time, depending on the number and size of the files to be encrypted. The decryption key will be sent to a server that the attacker has access to, which he can later use for decryption.
- Ransom notes. After the encryption is complete, the victim will usually receive a ransom note that explains what has happened and provides instructions on how to pay the ransom. This note may be displayed on the victim’s screen or saved as a text file on the desktop or in various folders throughout the system.
- Payment. The ransom is usually demanded in cryptocurrencies such as Bitcoin, which makes it difficult to trace the payment back to the attacker. Once the payment is made, the attacker should provide the decryption key needed to unlock the victim’s files.
- Decryption. With the decryption key, the victim can now decrypt their files and regain access to their data. However, there is no guarantee that the attacker will actually provide the decryption key, and even if they do, there is no guarantee that the decryption process will be successful.
How is the data encrypted?
Now, what we are most eager to understand, the most important part of ransomware is that the code encrypts files. If we were to write ransomware code, what are the steps we would take to do so? How is encryption in ransomware being done?
Encryption is the process of converting data into a secret code, known as cipher text, to prevent unauthorized access. In the context of ransomware, encryption is used to encrypt files on a victim’s computer, making them inaccessible until a ransom is paid.
The next steps can be written in a variety of programming languages, depending on the individual and his technical abilities. Ransomware code is typically written in C and C++, but it can also be written in Python, Java, .NET, and Swift. It all depends on the targeted system and what you are the greatest at as a developer or hacker.
Here are the steps involved in the encryption process:
- Selection of Encryption Algorithm. The selection of an encryption algorithm is the first step in the encryption process. A mathematical method used to convert data from its original form to cipher text is known as an encryption algorithm. There are numerous encryption methods available, including AES, DES, and Triple Data Encryption Standard (3DES).
- Generating the Encryption Key. An encryption key is generated after an encryption algorithm is chosen. The encryption key is a randomly generated string of bits that the algorithm uses to encrypt and decrypt data. The strength of encryption is determined by the length of the key. A longer key length improves security but necessitates more computing capacity to encrypt and decrypt data.
- Encryption of Data. The encryption process begins with the conversion of data from its original form into cipher text, which is accomplished with the help of an encryption key and algorithm. The method reads plain text data in fixed-sized blocks and creates a corresponding block of cipher text for each block. The procedure is repeated until all the data has been encrypted.
- Storing the Encrypted Data. The encrypted data is saved afterwards on the victim’s computer, or a remote server controlled by the attackers.
- Removing the Original Data. After the data has been encrypted, the original data is typically deleted from the victim’s computer to prevent recovery using data recovery tools. More advanced ransomware software even re-writes the data before deleting it so it cannot be recovered.
- Ransom Note. Finally, the attackers will show a ransom letter demanding payment from the victim in exchange for the decryption key, which will allow access to the encrypted data to be restored.
Mac OS “PoC” Ransomware
So, I attempted to develop a basic PoC MacOS ransomware. Here is what I did after following the procedures outlined above, and how it turned out.
It is designed to be simple and easy to understand the concept of MacOS file encryption that is headed to how ransomware encryption works. It demonstrates basic file encryption and decryption using Python and the cryptography library. However, please note that this script is not suitable for real use.
1. Import necessary modules
- ‘os’: Used for working with directories and files in the operating system.
- `subprocess`: Not used in this script, so it can be removed.
- `cryptography.fernet`: Imports the `Fernet` class, which provides symmetric encryption using the cryptography library.
2. Define the ‘generate key’ function
- This function generates an encryption key and saves it in a specified directory.
- It first generates a key using `Fernet.generate_key()` and creates a key file path in the specified directory.
- It then writes the key to the key file and prints the location of the created key.
3. Define the ‘encrypt directory’ function
- This function recursively encrypts all files in a specified directory using a given key.
- It first creates a Fernet object with the provided key.
- It then walks through the directory, encrypting each file and saving it with a “.lukax” extension.
- After encrypting each file, it deletes the original file.
4. Define the ‘decrypt directory’ function
- This function recursively decrypts all files in a specified directory.
- It first creates a Fernet object with the provided key.
- It then walks through the directory, decrypting each file with a “.lukax” extension and saving it without the extension.
- After decrypting each file, it deletes the encrypted file.
5. Ask the user for their choice of operation (encrypt or decrypt)
- #If the user chooses to encrypt:
- Ask for the directory to encrypt and the directory where the key file should be saved.
- Generate the encryption key and save it in the specified directory.
- Encrypt the specified directory with the generated key.
- #If the user chooses to decrypt:
- Ask for the directory to decrypt and the location of the key file.
- Load the encryption key from the specified key file.
- Decrypt the specified directory with the loaded key.
- #If the user enters an invalid choice, print an error message.
The script in action
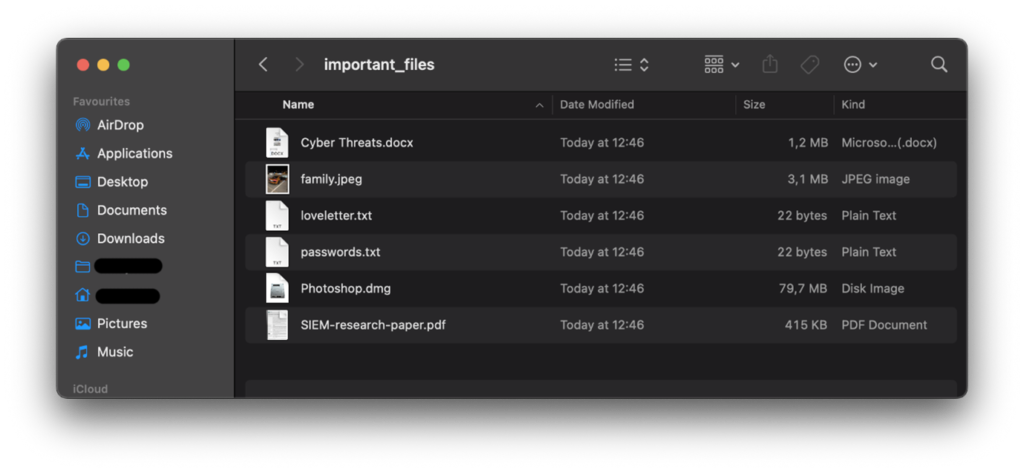
First to display the content of the directory that I will attempt to encrypt. As you can see there are several types of files in the dir, by type and size. The goal is to make each file type unreadable and later decrypt it.
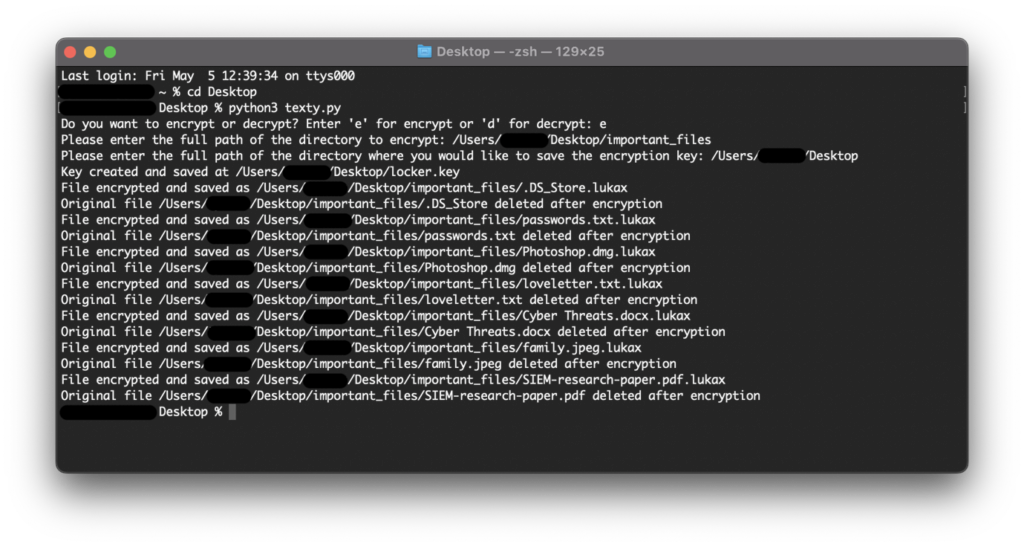
Here I ran the script, called texty.py. As mentioned before, it asks the user to encrypt or decrypt. We did not encrypt anything yet, so I chose ‘e’.
The next step was to enter the full file path to encrypt the files, and after that the path in which we will store the key.
After doing to, the script does its things and starts encrypting and deleting files one by one.
The deleted files cannot be found in the bin.
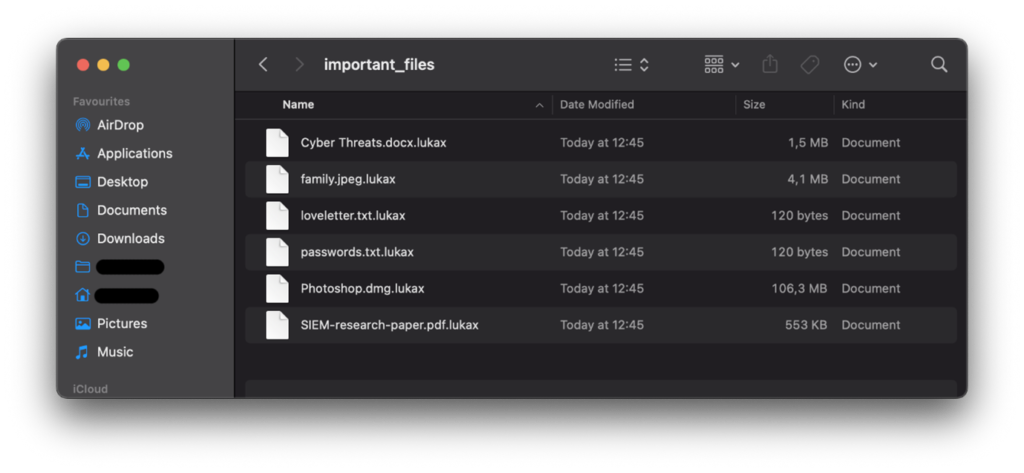
Here is what the directory looks like after running the script. Each of the files has an extension of .lukax. None of the files are readable and we cannot access the deleted files.
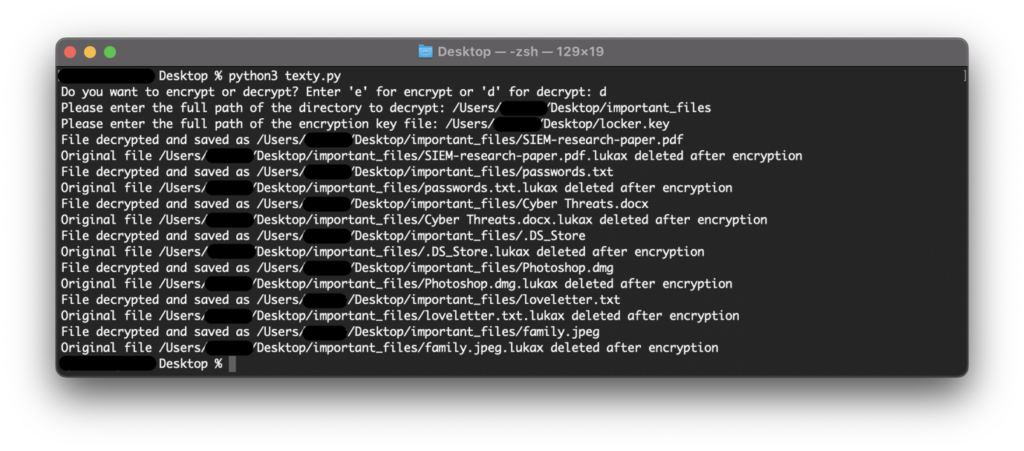
Now I will re-run the script and choose the other option ‘d’ which is for decrypting files. We must put in the full path of the directory which we want to decrypt and the full path to the key that needs to be used for decryption. The script then starts decrypting files one by one and deleting the encrypted files as well.
Going back to the folder, we can see that the files are back in their original state!
I hope that the macOS ransomware demonstration has given you fresh insights into the workings of encryption and a broad understanding of the stages required in constructing harmful software. It is critical to underline that this demonstration is intended for instructional reasons and that this knowledge must be used ethically and responsibly. Understanding attacker strategies can help us better protect ourselves and our systems from cyber threats. We can help to create a more secure digital world for everyone by continuing to educate ourselves on the subject. Do you want to raise awareness about Cyber Security among your organisation’s employees? Our experts can also provide an awareness session on site. For example, during a meet the hacker session they show how a hacker works.
Conclusion
This Proof-of-Concept malware is a small Python script that executes a portion of what true malware code would do. The code could be packaged as a .dmg file, which is a basic macOS installation file. The dmg file could be packed to look like a cracked app that people want to download, then it is easy for the user to accept the prompt by Apple which is the only protection he has against viruses. If such a program were downloaded from the internet the user would get the prompt “*AppName* is an application downloaded from the Internet. Are you sure you want to open it?” After clicking on open and inputting the password, it is done. The computer would be infected. In the next blog post we will cover the best practices in the protection against malware. In the previous blog post, you were able to read more about the history of malware and the current situation.
Immediately mitigate malware risks or create more awareness about Cyber Security? The Cyber Security experts of Cuccibu are ready to help! For example, we can set up an awareness programme to raise awareness about the dangers of malware among employees. We can also implement crisis simulation and/or provide SIEM/SOC monitoring. SIEM/SOC monitoring makes it possible to act as quickly as possible in case of infection and stop the attack immediately. Want to know more about what we can do? Feel free to contact us at sales@cuccibu.nl. We will be happy to tell you about the various possibilities.
In addition, we would like to draw your attention to our “Meet the Hacker” session on 27 october in our new office in Rijswijk. During this interactive afternoon, in the form of a demonstration, we will create insights into a hacker’s modus operandi and highlight the associated dangers. You can register via our website, see here.
Reduce Risk, Create Value!
jun
Cuccibu Inhousedagen Consultancy
Tijd
11.30 uur - 16.30 uur
Locatie
Kantoor Eindhoven