The History of Malware
Introduction to Malware
The digital age has drastically changed the way we live our lives. Thanks to our digital devices, we have instant access to information, entertainment, and communication. However, this convenience also comes with the risk of malware or malicious software. Malware is software designed to harm or exploit digital devices such as computers, smartphones, and tablets. Malware is a constant threat in today’s digital landscape, with serious consequences for individuals and businesses. In this blog post, which is broken down into 4 pieces we’ll look at the history of malware.
The History of Malware
1971 – The first proof of concept “virus”
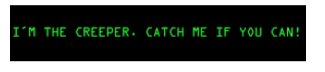
In 1971, a programmer named Robert Thomas developed the first known computer virus, “Creeper” The program was not intended to be malicious, but rather to demonstrate how easily data could be transferred between different computer platforms. Creeper could duplicate itself and travel across ARPANET, a network created in 1967 before the internet, as we know it today existed. ARPANET allowed remote connection between computers, so Robert created the PoC on that then new technology. Connected computer systems, displaying the message “I am the creeper, catch me if you can!” on infected PCs.
After Creeper was created, another tool called “Reaper” was developed to eliminate the Creeper infection. This was the first example of anti-malware software and laid the foundation for the ongoing conflict between malware producers and those who want to fight it.
The term “computer virus” was not coined until the 1980s. The first viruses were produced as experiments by computer scientists to illustrate the possibility of self-replicating code. However, as computer technology advanced and the Internet became more widespread, viruses evolved from simple experiments into a real threat to computer security.
1982 – The first Mac virus
Contrary to popular belief that “Macs are not susceptible to viruses,” the first computer virus discovered in the wild, named “Elk Cloner,” was designed to attack Apple II computers. Rich Skrenta, a high school student, invented Elk Cloner to prank his buddies. Apple II computers were used to spread the malware. When an infected hard drive was booted, the boot sector virus spread. The virus lived in memory until it found a clean disc to infect. After every 50th boot, the malware displayed a poem on the screen:
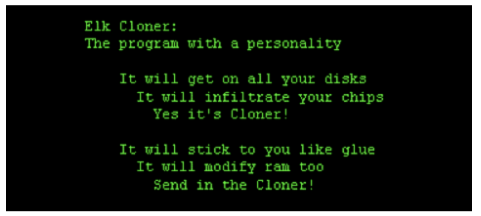
Elk Cloner did not cause any serious damage to the affected systems, but it showed that Macintosh computers are vulnerable to viruses and malware just like any other system.
1986 – The first PC virus, The Birth of the First PC Virus: The Story of Brain Virus
The first PC virus, known as Brain Virus, was released into the world in January 1986. Two brothers from Pakistan named Basit and Amjad Farooq Alvi are believed to have invented the virus.
The Brain virus was a boot sector virus that infected the boot sector of floppy disks in IBM -compatible systems. When an infected floppy disk was inserted into a computer, the virus copied itself to the hard disk and then infected all other floppy disks inserted into the computer.
The virus was generally harmless at the time, but caused some difficulties for computer users. The virus changed the disk label of an infected disk to “©Brain “, making it easier for users to identify the affected devices. The malware also contained the phone number and address of Brothers, which researchers used to track down the originators of the infection.
The Brain virus was not developed with malicious intent, but as a form of copy protection for the medical software produced by the Alvi brothers. They wanted to prevent unauthorized copies of their software from being made. The virus was intended to spread primarily in Pakistan, but due to the global nature of the computer industry, it quickly spread around the world.
The discovery of the Brain virus triggered widespread concern about computer security. Previously, viruses were considered a theoretical harm to computer users, but the Brain virus showed that viruses were a real and present threat.
Fortunately for many, it was not a harmful infection. It hid a certain sector, preventing the computer from booting, and displayed a message with the contact details of the Farooq Alvi brothers, who were trying to find a remedy. They claim that they want affected people to contact them to find out how to acquire their software legally.
Within the notification, it stated:

Their brilliant plan was so successful that the brothers were flooded with calls from all over the world.
Rise of Antivirus Software
The first antivirus program was also inspired by the Brain virus. McAfee Associates was founded in 1987 to develop antivirus software for personal computers. The company’s first product, VirusScan, was designed exclusively to detect and eradicate the Brain virus.
In summary, the Brain virus was a key event in computer history. It was the first PC virus to demonstrate the dangers of viruses and the need for anti-virus software. While the virus itself was relatively harmless, it paved the way for other destructive viruses to emerge in the years that followed. The Brain virus reminds us of the importance of computer security and the need to be on guard against attacks.
Soon enough malware developers changed their intentions of harmless malware and began using computer viruses to cause damage, steal information, or disrupt computer systems. In the late 1980s and early 1990s, malware developers transmitted viruses on floppy disks, and as the Internet became more popular, they spread via email attachments and infected downloads.
1988 – The first worm, the Morris worm
The difference between a virus and a worm is that a worm does not require human interaction to spread. The world’s first worm was born more than 30 years ago. The Morris worm was named after its creator, Robert Morris. This worm was not harmful. It was developed as a proof-of-concept to determine if independent reproduction was possible.
It was the first large computer worm to capture the public’s attention. It took advantage of flaws in the Unix operating system to propagate quickly throughout the Internet and cause major disruption to computer networks. The Morris worm brought computer security to the forefront, emphasizing the need for greater security procedures to prevent such attacks. It also resulted in the formation of the first Computer Emergency Response Team (CERT) to respond to and prevent future crises.
Mr. Morris was the first person found guilty under the Computer Fraud and Abuse Act. However, he later became a successful entrepreneur and obtained a permanent position at the Massachusetts Institute of Technology (MIT).
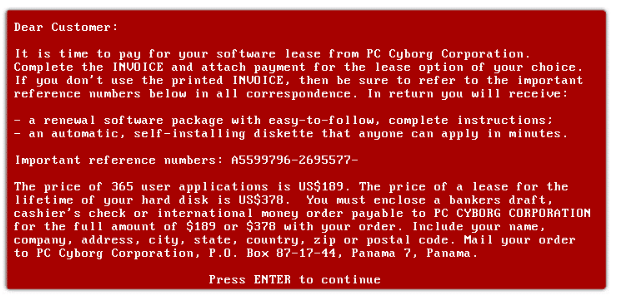
1989 – World first ransomware
Before 1989, when the first ransomware appeared on the scene, most viruses infected computers for “fun,” to demonstrate the computer’s capabilities, PoCs. Today, however, computer viruses and malware are used with the express purpose of causing damage, stealing data, and making financial gains.
The AIDS Trojan was not widespread and had limited impact, but it signaled the beginning of a new type of cyberattack that would become more common in the years to come. The AIDS Trojan served as a warning that cybercriminals will do anything to extort money from their victims, and the threat of ransomware has only increased since then.
Dr. Joseph Popp was credited with developing the AIDS Trojan, and he insisted that he did so to donate the money he made from the ransomware to AIDS research. However, according to some reports, he was angry at the World Health Organization for denying him a contract. Strangely, Dr. Popp did not send any of his disks to American scientists.
The malware’s encryption key read “Dr. Joseph Lewis Andrew Popp Jr.” according to forensic analysis. After being arrested and charged in the United Kingdom, Dr. Popp was later found mentally incompetent and sent back to the United States.
In the early 2000s, more cases of malware started popping up to the surface of the internet. Whitin that short time, malware evolved, and most malware use cases are a type of malware that encrypts user data in the exchange of a payment to decrypt that data. The malware is called ransomware which you might guess as it is seeking a ransom from the victim.
Conclusion
The of malware saw a big shift in the early 2000s. Although curiosity and exploration were the initial driving forces, the motives evolved towards pure harm and criminal intent. The majority of malware is created for financial gain, targeting individuals, organizations, and governments. In the next blog post, we will cover the current malware situation, covering different types and some of the most memorable, harmful malware in the past 20 years. In the third blog, we talk more about the technical aspects of malware and in the fourth blog, we give tips on how to protect your organisation against malware.
Immediately mitigate malware risks? The Cyber Security experts of Cuccibu are ready to help! For example, we can set up an awareness programme to raise awareness about the dangers of malware among employees. We can also implement crisis simulation and/or provide SIEM/SOC monitoring. SIEM/SOC monitoring makes it possible to act as quickly as possible in case of infection and stop the attack immediately.
Want to know more about what we can do? Feel free to contact us at sales@cuccibu.nl. We will be happy to tell you about the various possibilities.
Reduce Risk, Create Value!